Cyber Resilience Latest 2022
What is Cyber Resilience?
Cyber resilience is the ability of an organization to enable business acceleration (enterprise resiliency) by preparing for, responding to, and recovering from cyber threats. A cyber-resilient organization can adapt to known and unknown crises, threats, adversities, and challenges.
The ultimate goal of cyber resiliency is to help an organization thrive in the face of adverse conditions (crisis, pandemic, financial volatility, etc.).
What is enterprise resilience?
Enterprise resilience is the ability for an organization to address strategic, financial, operational, and information (cyber) risk in a manner to drive business growth, profitability, and sustained modernization (digital transformation).
Shift to cyber resilience: 7 steps to a better security approach
1-Invest in SOAR to improve detection and response times
Security orchestration, automation, and response (SOAR); security information and event management (SIEM) software; and managed detection and response and services can help an organization accelerate incident response with automation, process standardization, and integration with existing security tools, the report noted.
2- Adopt zero trust to control access to sensitive data
Only 35% of organizations surveyed have implemented a zero-trust security approach. However, those in the mature stage of their zero-trust deployment had an average breach cost that was $1.76 million less than organizations not using the approach.
As organizations have shifted to incorporate remote work and more disconnected, hybrid, multi-cloud environments, a zero-trust strategy can help protect data and resources by making them accessible only on a limited basis and in the right context, the report noted.
3- Stress-test your incident response plan to boost resilience
The facts here speak for themselves: Organizations in the Ponemon study that had incident response teams and tested their incident response plans saw an average total cost of a data breach that was $2.46 million less than organizations that experienced a breach without an IR team or a tested IR plan.
4- Use tools to protect and monitor endpoints, remote employees
Unified endpoint management and identity and access management products and services can help provide security teams with deeper visibility into suspicious activity on company-owned and BYOD laptops, desktops, tablets, mobile devices, and IoT devices, according to the report, including endpoints the organization doesn’t have physical access to, speeding investigation and response time to isolate and contain damage caused by a breach.
5- Invest in governance, risk management, and compliance
Having an internal framework for audits, evaluating risk across the enterprise and tracking compliance with governance requirements can help improve an organization’s ability to detect a data breach and escalate containment efforts, the report explained.
6- Embrace open security architectures and minimize complexity
Security tools with the ability to share data between disparate systems can help security teams detect incidents across complex, hybrid, multi-cloud environments, the report noted. A managed security services provider can also help simplify security and risk with continuous monitoring and integrated solutions and services, it added.
7- Protect sensitive data in the cloud with policy and encryption
The report recommended using data classification schema and retention programs to help bring visibility into and reduce the volume of the sensitive information that is vulnerable to a breach, and protect it using data encryption and fully homomorphic encryption.
It added that vulnerability scanning, penetration testing, and red-teaming should be used to help identify cloud-hosted database vulnerability exposures and misconfigurations.
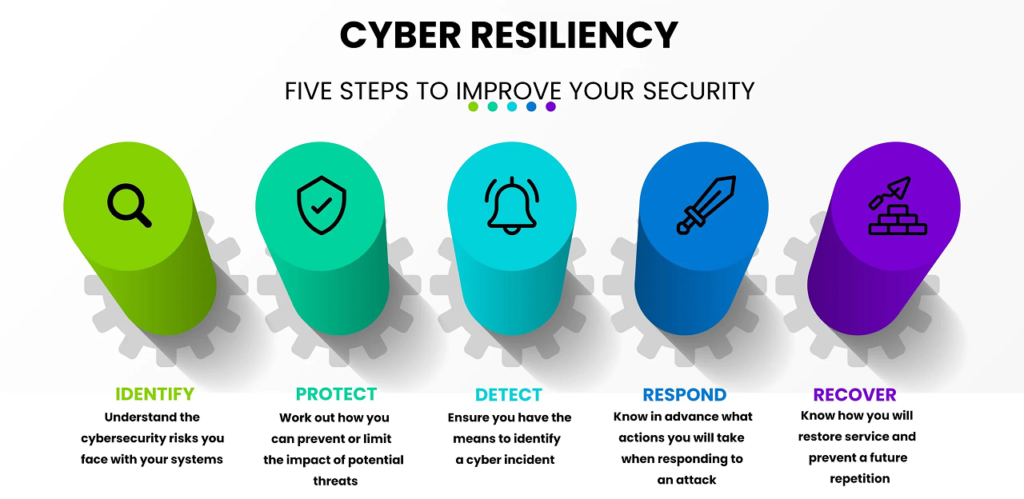
Resilience is the way forward
Compromised credentials are the most common attack vector for enterprises experiencing a data breach, according to the report, a finding corroborated by the 2021 Verizon Data Breach Investigations Report. Verizon identified credentials as the most common data type found in intentional breaches this year—in a staggering 61% of breaches. Once a network was infiltrated, customers’ personally identifiable information (PII) was stolen in close to half of the cases.
The Ponemon report says that companies that use security solutions based on artificial intelligence, machine learning, zero trust, analytics, and encryption all mitigated the potential cost of a breach. Those technologies and security controls saved firms, on average, between $1.25 million and $1.49 million. Organizations with fully deployed security AI and automation saw breach costs that were $3.81 million less than organizations without it.
If you’re going to buck the trends in these data breach reports, your security team needs to implement as many of the recommendations above as possible, and reduce the mean time to detect and control cyber threats. Your organization’s resilience depends on it.
How does cyber resilience work?
On the other hand, cyber resilience refers to the company’s ability to mitigate damage and get mission-critical systems up and running quickly following a breach. Cyber resilience can refer to both external threats, such as hackers and ransomware, as well as internal threats like accidental deletion.
How do you achieve cyber resilience?
Follow best practices and take advantage of security systems and tools, such as:
1-Proactive security
Anti-malware protection
Anti-virus
Cyber risk quantification
Email security
Endpoint protection, endpoint security
Ransomware protection
Risk-based vulnerability management
Unified asset inventory
URL filtering
2-Preventative security
Backup
Education
Encryption
3-Security management systems
Data Loss Prevention (DLP)
Identity access management (IAM)
Multi-factor authentication (MFA)
Patch management tools
Security information and event management (SIEM)
Cyber Resilience vs. Cybersecurity
There is a persistent confusion between cybersecurity and cyber resilience and their relationship. Cyber resiliency is not a replacement for cybersecurity. They are complementary. Cyber resiliency techniques are used to support and enhance cybersecurity measures.
Cybersecurity
Cybersecurity is a defense strategy consisting of a combination of technologies and processes that are designed to enforce policies and protect systems, networks, data, and IT infrastructure from cyber threats (e.g., malware, ransomware, hacktivism, malicious insiders). Effective cybersecurity reduces the risk of cyber-attacks and protects resources and assets from loss, theft, or damage.
Cyber Resilience
Cyber resilience combines cybersecurity and operational resilience. It refers to an organization’s ability to consistently prevent, respond to, mitigate, and successfully recover from cyber-related incidents. This includes threats and attacks from cyber-criminals and malicious insiders, and also catastrophic system failures from misconfigurations and accidental deletions. Cyber resilience can be applied to both external and internal threats.
Cyber resilience strategies assume that attackers have an advantage in reaching their target with innovative tools and approaches, use of different malware variants, and the element of surprise. This concept helps businesses prepare, prevent, respond, and successfully recover and resume their pre-attack business processes and business operations. In short, cyber resilience requires the business to think differently and be more agile in order to anticipate and mitigate attacks.
Business leaders across the globe realize that no singular cybersecurity solution is sufficient enough to tackle today’s sophisticated and constantly evolving cyber-attacks. Despite ramping up your defenses, cyber-criminals can still take advantage of human error or find loopholes and penetrate your company’s network and IT systems. This is where using using proactive tools with automation and AI is key to establishing cyber resilience across the organization.
Read More About NIST
Buy From Amazon
