Latest Non-OWASP vulnerabilities 2022
What are the other Non-OWASP vulnerabilities?
OWASP states very clearly in their methodology that the Top 10 list is, by definition, only a subset of important security issues and organizations should be aware of additional security risks.
You should maintain awareness of other new vulnerabilities discovered in the wild such as the Log4Shell Vulnerability, which was disclosed in December 2021.
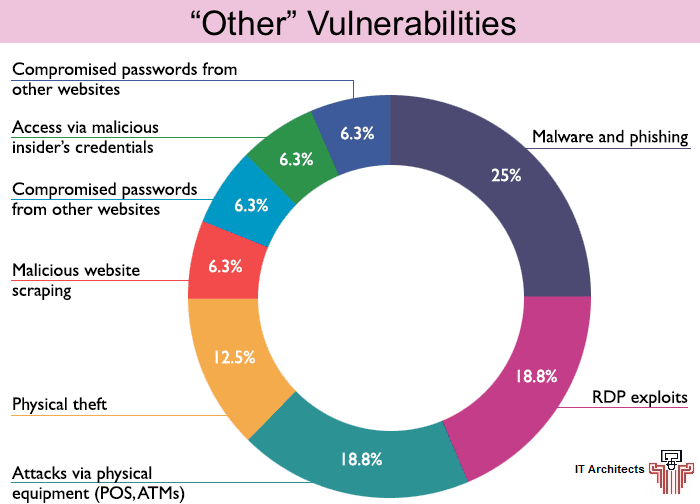
Which other threats were a root cause of Top 50 Breaches and were outside the scope of the OWASP Top 10?
Malware and phishing: 4 breaches
RDP exploits: 3 breaches
Attacks via physical equipment (POS, ATMs): 3 breaches
Physical theft: 2 breaches
Malicious website scraping: 1 breach
Compromised passwords from other websites: 1 breach
Access via malicious insider’s credentials: 1 breach
Data leaked by third parties with access: 1 breach
It’s interesting to note, for example, that malware and phishing, often considered as an end-user security problem and not an issue for web applications, was responsible for four of the top 50 data breaches, while A1—Injection, OWASP’s #1 security vulnerability, was responsible for the same number of breaches.
Also read – Click Here
You can also go- https://www.facebook.com/theitarchitects

1 Comment